This is part three of a three-part series on product infrastructure security.
- Part 1: How to assess your product infrastructure security
Part 2: How to secure your product infrastructure security
The attack vectors in the cloud are constantly evolving. These attacks frequently use unpatched vulnerabilities and insecure configurations to gain access to your systems. Quick and effective detection and proactive remediation is the key. As a startup building your business in the cloud, becoming the target of a malicious attack can set you back from your peers. Microsoft Defender for Cloud has built in controls and integrated tools that can protect you from such predicaments.
In this blog series, we started off by discussing the relevance of security posture management and how to get started with the service. In the second part, we looked at the steps to get started with some of the key features of Microsoft Defender for Cloud that will help you get started with the service. In the concluding part of this series, we will deep dive further into the capabilities of Microsoft Defender for Cloud that will help protect your environment from malicious attacks.
Assess security posture through secure score
For startups working in highly regulated industry verticals, ensuring compliance can involve extensive efforts. The option to download a certificate demonstrating how secure your infrastructure and services are will help make this process go more smoothly. The secure score provided by Microsoft Defender for Cloud based on leading compliance standards puts forth the easiest solution for this.
What is Microsoft Secure Score?
The security status of your deployments is continuously assessed by Microsoft Defender for Cloud and the outcomes are quantified as a secure score. The secure score is displayed as a percentage, and the service also displays the security findings that contribute to the score.
The Secure score can be viewed from Microsoft Defender for Cloud > Security posture. The security posture of different connected environments can also be viewed from here:
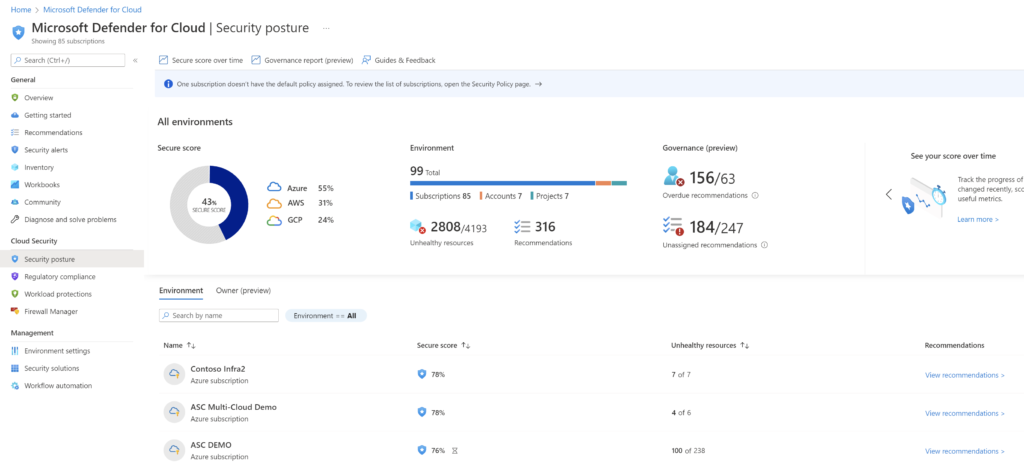
Click on Recommendations to see the controls and recommendations for each environment. The view also shows the maximum score for each control, the current score and potential score increase that is possible by remediating the findings.
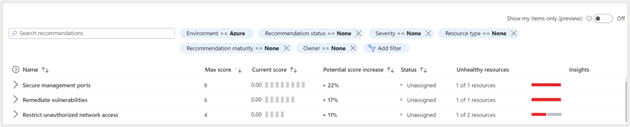
You can expand the security control to see the recommendations associated with it. For example, shown below are the recommendations associated with the control “Secure management ports.” This control provides guidance on securing the management ports associated with your resources. If left unprotected, these ports can be targeted by brute force attacks to gain access to the environment.
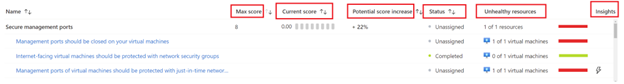
Max score: If all findings are remediated, the maximum possible score will be 8. The score is associated with a control based on its relevance to the respective environment. The recommendations associated with the control having the highest score should be prioritized first.
Current Score: It shows the current score based on the number of resources that are already in line with the recommendations.
Potential score increase: This section shows the percentage by which the score can be increased by remediating the recommendations.
Insights: It gives you additional information about the respective recommendations. The guidance provided can be used to fix the findings. You can also set up policies that will either rectify the problem if someone creates a non-compliant resource or altogether prevent the creation of resources with this issue.
Secure score calculation: The score associated with a single security control is calculated using the following formula
![]()
The score associated with each control rolls ups to provide the secure score of the Azure subscription or other connected cloud environment using the below formula:
![]()
When there are multiple subscriptions or connected AWS/GCP environments the overall security posture is calculated using the following formula
![]()
Note that Microsoft Defender for Cloud assigns a weight to each environment depending on parameters such as the number of resources in that environment.
Resolve threats and improve secure score
Microsoft Defender for Cloud protects your subscriptions by implementing security initiatives. One or more security policies are included in these initiatives. Each of these policies yields a security recommendation for strengthening your posture.
Security policy: Azure policies help implement subscription wide restrictions like usage of tags, naming convention, allowed regions. A security Policy uses the same constructs to create a set of rules for controlling certain security configurations. Defender for Cloud policies can either be “Audit” or “Enforce” policies. ‘Audit’ policies, inspect and report on certain security configurations. “Enforce” policies on the other hand that can be used to enforce secure settings.
Security initiative: A Microsoft Defender for Cloud security policy initiative is created in Azure policy and is a collection of security policies groups for a specific purpose. Azure Security Benchmark is the default initiative assigned by Microsoft Defender for Cloud for all subscriptions. It is built based on industry standard controls derived from National Institute of Standards and Technology (NIST) and Center for Internet Security (CIS). In addition to this, you can also create initiatives based on industry compliance standards.
Security recommendation: Depending on the security initiative and the policies included in it, Microsoft Defender for Cloud continuously analyzes your target environment and provides security recommendations.
Review recommendations
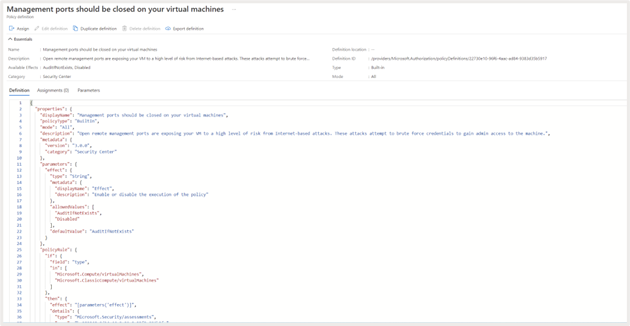
Let’s take a closer look at one of the security recommendations, “Management ports should be closed on your virtual machines.”
If you click on the recommendation, you can see additional information, including. severity, description of the recommendation, remediation steps, affected resources, etc.
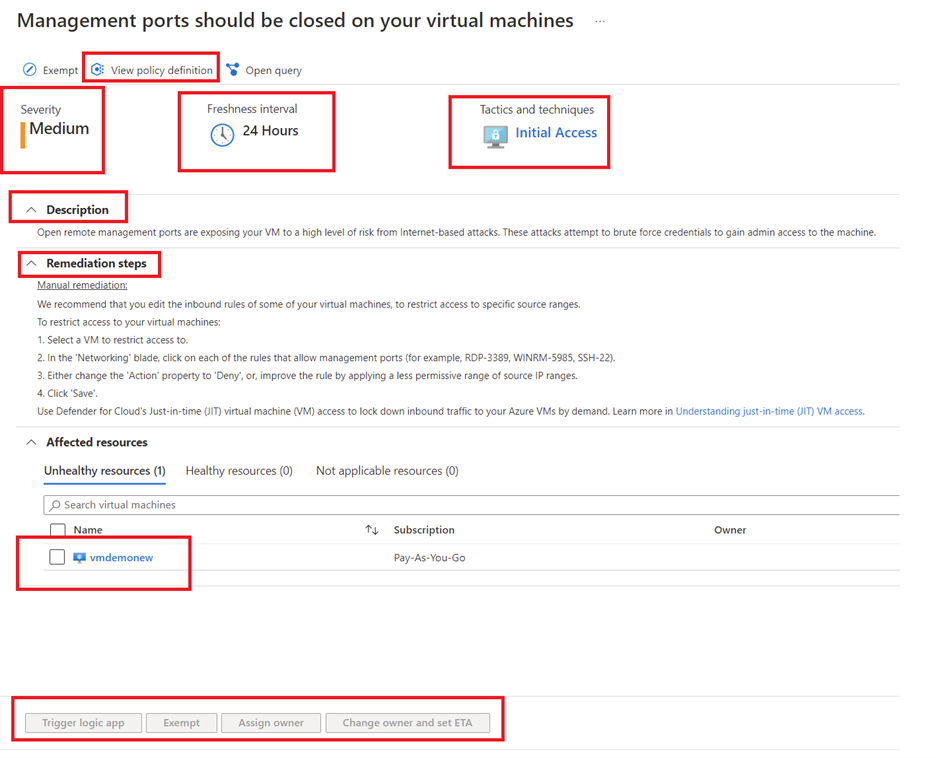
View policy definition
You can click on “View policy definition” to see details of the policy associated with the recommendation.
Severity
This defines the severity of the recommendation, that helps with prioritization of the recommendation.
Freshness
Gives insights on when the recommendation was issued.
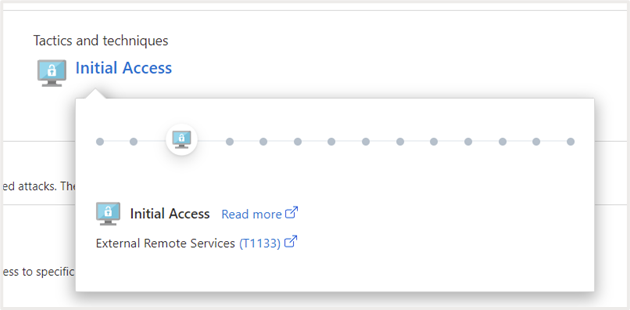
Tactics and Techniques
This provides additional information on MITRE ATT&CK tactics and techniques related to the recommendation. You can click on the link to get additional information.
Description
Explains why the control is important and how it can be exploited to attack your environment.
Remediation steps
Provides step by step guidance on how to implement the recommendation. For example, the remediation steps in this case are as follows:
Manual remediation
We recommend that you edit the inbound rules of some of your virtual machines, to restrict access to specific source ranges.
To restrict access to your virtual machines:
- Select a VM to restrict access to.
- In the ‘Networking’ blade, click on each of the rules that allow management ports (for example, RDP-3389, WINRM-5985, SSH-22).
- Either change the ‘Action’ property to ‘Deny’ or improve the rule by applying a less permissive range of source IP ranges.
- Click ‘Save’.
Use Microsoft Defender for Cloud’s Just-in-time (JIT) virtual machine (VM) access to lock down inbound traffic to your Azure VMs by demand. Learn more in Understanding just-in-time (JIT) VM access.
Affected resources
Here the resources for which the recommendation is applicable are listed. They are segregated as follows:
- Unhealthy resources: Shows the resources where the issue needs to be remediated
- Healthy resources: Shows resources where the issue is already remediated or those not impacted by the issue
- Not-applicable resources: Some resources cannot be evaluated against the recommendation and are marked as “not applicable resources”. This could be because of corrupted VM extensions, lack of scanner, etc. The reason why the evaluation is not done will also be listed
Action
You can select one of the affected resources and choose to remediate the action by Triggering a logic app or assign the owner to take action . You can also choose to Exempt the resource from this recommendation by selecting the “ Exempt” option wherever applicable to align with organizational security standards.
Fix recommendations
Microsoft Defender for Cloud can fix some of the recommendations directly from the console. Let’s explore how to do that for the recommendation “Machines should have a vulnerability assessment solution.”
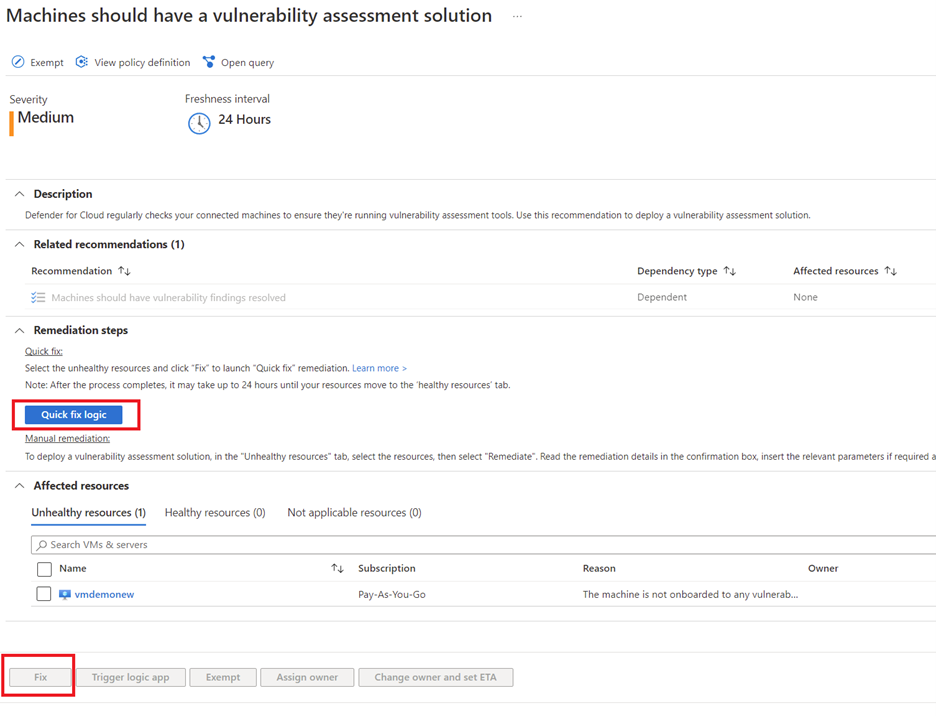
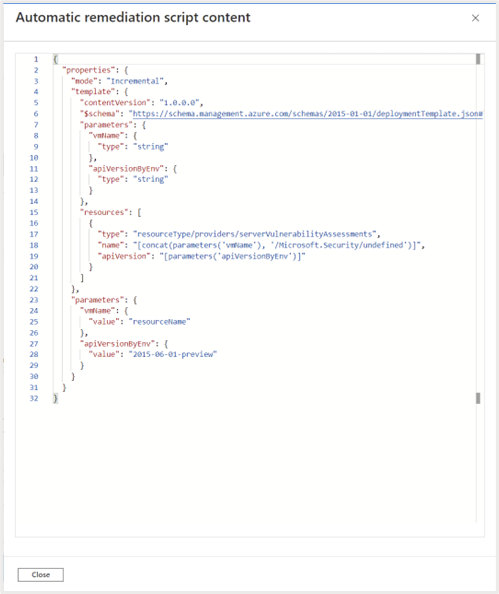
Quick fix logic
You can click on this link to view the remediation logic/script that will be used to fix the issue
To fix the issue select the unhealthy resource and click on “Fix”. This is initiate process of deploying vulnerability management solution on the resource.
How to investigate resource health
Microsoft Defender for Cloud provides a consolidated view of resource health and recommendations associated with it. You should have Resource Group contributor to view this, browse to Microsoft Defender for Cloud > Inventory.
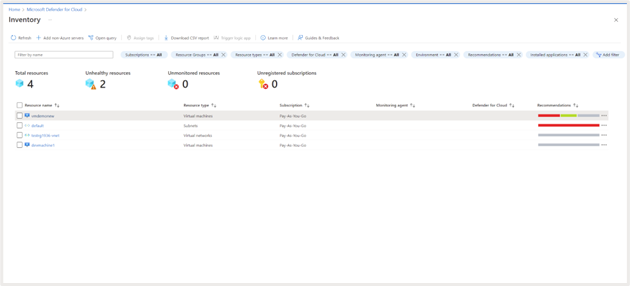
Click on a specific resource to view the resource health. You will get a view of recommendations, alerts and installed applications for that resource.
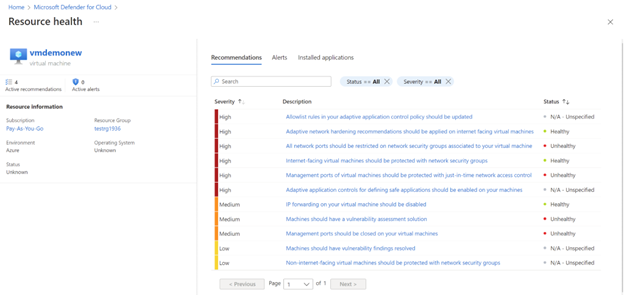
Click any of the recommendations to take remedial action.
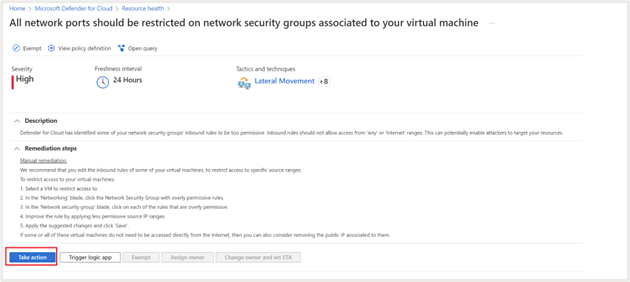
Click on “Take Action” or “Fix” (for some recommendations) to implement the remediation steps as discussed in the earlier section
View and respond to security alerts
Getting timely security alerts on detected attacks go a long way in preventing catastrophic events. Microsoft Defender for cloud uses advanced threat analytics and threat intelligence capabilities that can alert you about infiltration attempts and malicious activities in your environments. You can get a unified view of security threats detected in your environment, their severity and guidance on remediation steps once you have Microsoft Defender for cloud enhanced security features enabled.
To view detected security alerts, browse to Microsoft Defender for Cloud > Security alerts.
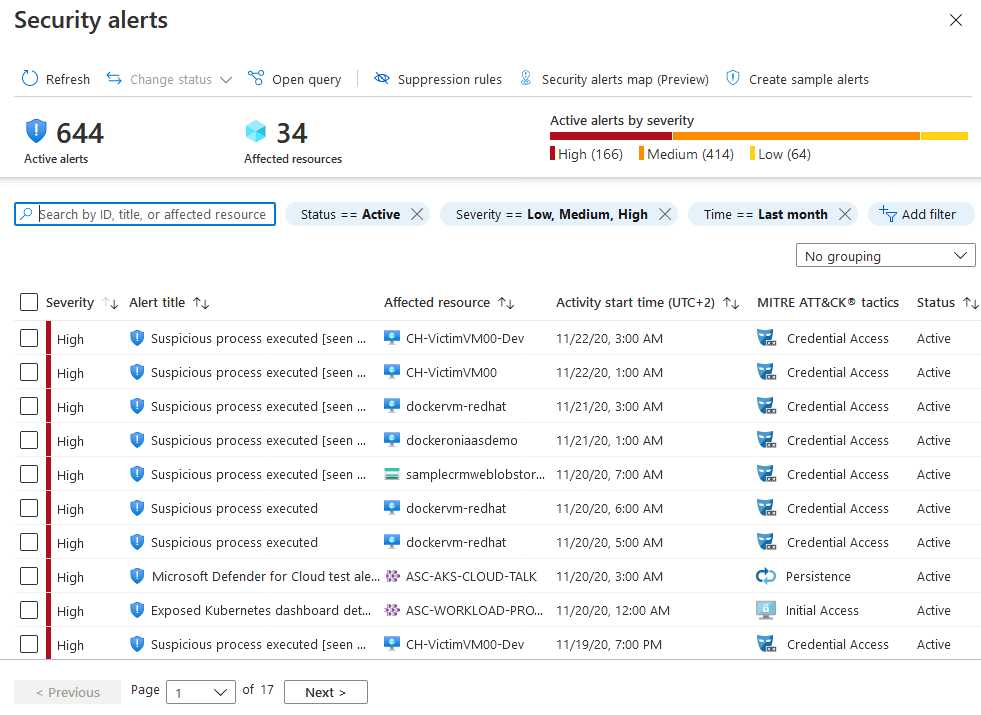
The alerts presented on this page are categorized as high, medium, low, or informational, depending on Microsoft Defender for Cloud’s level of confidence in the malicious intent behind the activity that triggered the alert. It helps you prioritize and take action on the alerts.
- High: Indicates a high probability of the resource being compromised by an attack and should be immediately prioritized for remediation.
- Medium: Indicates a medium to high malicious intent detection, usually originating from anomaly-based detections or machine learning algorithms
- Low: These are low priority events that may or may not be related to an attack. Blocked attack attempts are also displayed as Low severity if it needs to be looked into
- Informational: These are events that are not malicious but should be investigated contextually to understand if it is related to any other threats.
Let’s take a closer look at one of the alerts and understand how the remediation can be done:
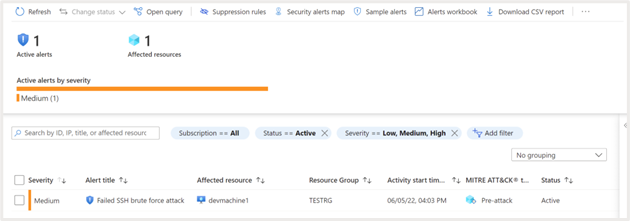
Click on the alert to view additional information about the attack:
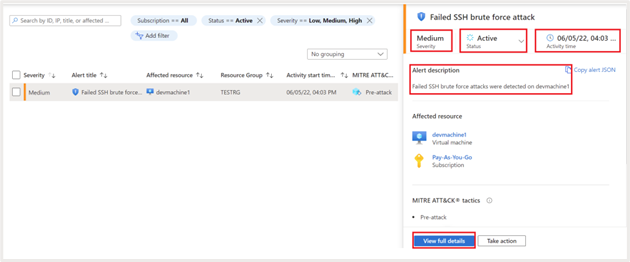
It shows the following additional details:
- Status of the activity. Detected alerts will be shown as “active” until necessary action is taken, and it is marked as Dismissed manually
- Description. Give additional information about the attack. In this case it is a Failed SSH brute force attack
- Time at which the attack is detected
- Severity of the attack
- Kill chain intent assessment based on MITRE ATT&CK metric
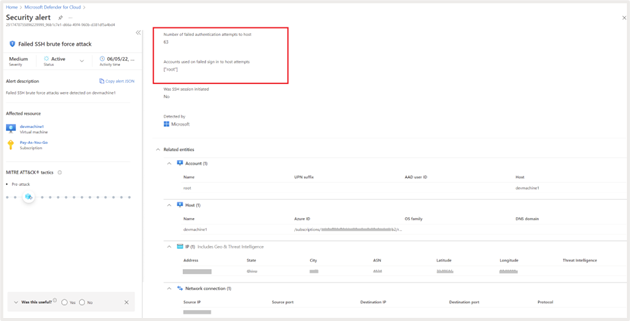
Click on “View full details” for additional info. It gives granular information on the number of times the attack happened; account used for the failed attempts etc. It also provides granular information about geo and threat intelligence, for example, the geography, ASN, latitude, longitude, etc., from which the attack originated.
Click on “Next: Take Action” to view guidance on the remediation steps to be taken.
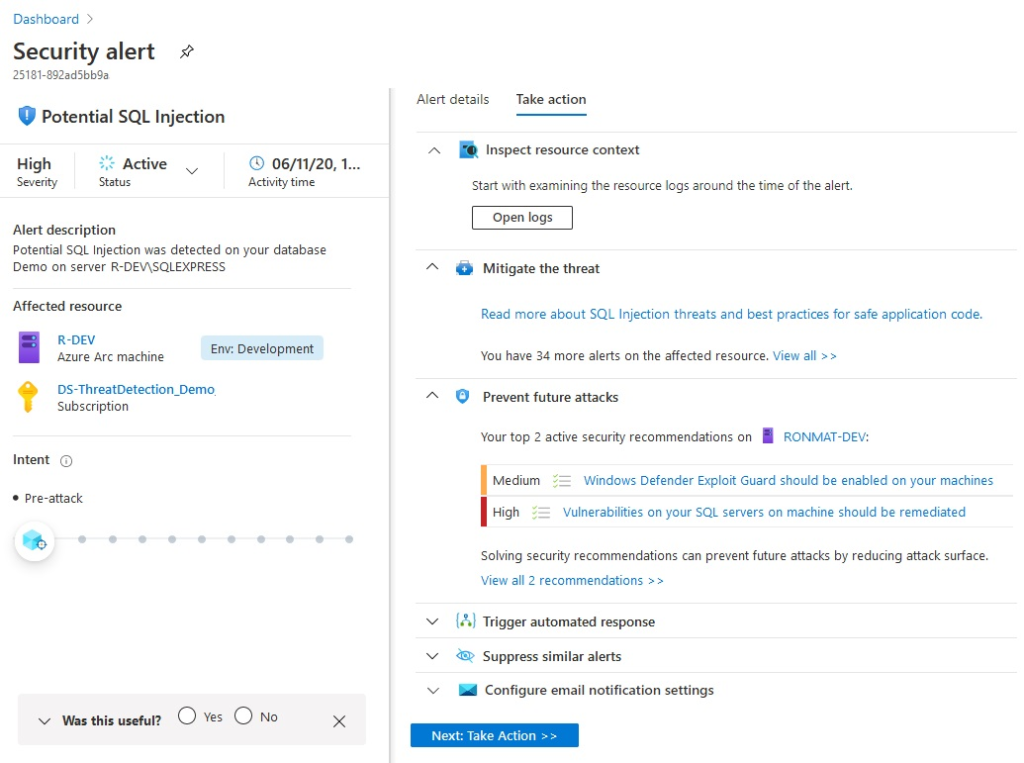
You can view the logs generated around the time of events to identify correlated events by clicking on “Open logs.”
The steps to mitigate the threat are listed under the section “Mitigate the threat.”
Any hardening recommendations that can prevent such attacks in the future is listed under “Prevent Future attacks.”
If you want to trigger a logic app as response to the detection, it can be linked under “ Trigger Automated response.”
If you identify that the alert was a false positive you can create a suppression rule from under the “Suppress similar alerts” section.
You can configure email notifications to alert administrators of this security event from the “Configure email notification settings.”
Summary
Microsoft Defender for Cloud helps protect your multi-cloud and hybrid environments from existing and emerging threats. Using advanced threat detection capabilities, analytics and machine learning algorithms, Microsoft Defender for Cloud can provide comprehensive security for your workloads.
In this three-part blog series, we explored all these topics to give you a head start on your cloud security posture management journey. Startups with minimal investment in security manpower can easily leverage the capabilities of Microsoft Defender for Cloud to secure your applications irrespective of the cloud platform it is hosted in. All the way from quantifying the security posture using secure score, providing actionable recommendations and alerts to intimate the right stakeholders, Microsoft Defender for Cloud has got you covered.
To get started with Microsoft for Startups Founders Hub, sign up today.












