This is part one of a three-part series on product infrastructure security.
- Part 2: How to secure your product infrastructure security
- Part 3: How to defend your product infrastructure security
Startups are changing the face of the world as we know it with innovative and disruptive ideas, products, and solutions. Cloud is at the heart of innovation in startups, a companion on their growth trajectory, from idea through execution and then scaling. All it takes is a few clicks to deploy your application in the cloud and your business is live. In the fast-paced startup world, agility, and the pace at which you can provide services to customers will decide the fate of your startup. Cloud provides just that, a fully-fledged ecosystem of services at your fingertips.
The startup journey is exciting and there is a plethora of choices available in the cloud for those who embark on this journey. Hybrid and multi-cloud deployments have become the norm rather than the exception. Along with selecting the right fit solutions for scale from the different cloud platforms, it is also important to reinforce the security of your environments as you grow. Having the right security controls in place is non-negotiable for successful product adoption. The process might get overwhelming when resources are dispersed across multiple cloud platforms with varying security standards.
In this blog series we will investigate the different aspects of cloud security to keep in mind as you grow your business. We’ll examine the state of security from ground zero, beginning with an understanding of the current situation, strengthening security, and being proactive in preventing attacks.
Product security posture management: What, why and how
In its most basic form, product security posture describes the level of security of your cloud resources as well as the capabilities in place to detect and protect against insider and external threats. Let’s take a detailed look at the what, why and how of security posture management.
What is product security posture management and workload protection?
Security posture management helps gain visibility into the state of security of your product. Cloud security posture management (CSPM) is a cloud-based solution that helps quantify the security posture of your product against defined benchmarks. These benchmarks can be specific to organizations or aligned with industry compliance standards. The CSPM solution’s score provides a clear indicator of what works and what doesn’t in the applied security configurations. CSPM provides actionable insights about the state of security. You can drill down further to get workload specific protection recommendations to strengthen security posture.
Applications deployed in the cloud also need tailored protection from evolving threat vectors. Most often the attacks would be targeting specific vulnerabilities of the target cloud service. Cloud Workload Protection platforms (CWPP) ensure comprehensive and intelligent threat protection for your cloud services. While you continue to build and deliver cloud-based solutions, CWPP will continuously monitor the components involved and alert you about any anomalies or suspicious activities.
Why should you consider security posture management?
There are different kinds of cyber-attacks that are being reported every day, especially those targeting workloads in the cloud. Also known as threat vectors, these attacks tend to target cloud platform-specific vulnerabilities. Hence it is important to ensure that workloads deployed across multiple clouds are secured as per the security standards applicable to respective cloud provider standards. It is also important to note that the standards, tools, and practices could differ across different cloud platforms.
Gaining visibility into your deployments across different platforms and managing the cloud security posture could become challenging. Making sense of the alerts and tracking how threat is progressing in your environment would be a difficult chore. Your cloud platform management team might end up hopping between multiple tools and views to get these insights. A single pane of glass view of cloud security posture could save the day.
When it comes to security, the devil is in the details. You want to know the origin of a threat, its impact, and its proliferation across your cloud landscape in as non-abstract terms as possible. You also want to understand if all the checks and balances are in place when it comes to security configurations. Security misconfigurations leave the door open for threat actors to infiltrate your environment. This due diligence needs to be done not just in one cloud platform, but across all cloud platforms where your assets are deployed. CSPM tools can help achieve this.
How to access security posture
There are multiple tools available across cloud platforms to assess product security posture Microsoft Defender for Cloud is one such tool that provides CWPP and CSPM capabilities for workloads deployed in hybrid and multi-cloud environments. Easy to onboard and use, the solution is built into Microsoft Azure but is not restricted to Azure resources, which makes it stand apart from other solutions providing similar capabilities. It provides the much-needed single pane view of security of your cloud assets deployed across hybrid and multi-cloud environments.
Protecting workloads in such heterogeneous environments is often a multi-step process and Microsoft Defender for Cloud provides these capabilities as follows:
Continuous assessment of security posture
Microsoft Defender for Cloud does a continuous assessment of cloud resources and quantifies it as a secure score. This score is indicative of the cloud environment security posture. A lower score indicates that the security levels are at risk and needs additional remediation to improve the security. The scoring is based Azure Security Benchmark (ASB) standards, that provides holistic security best practices and recommendations for workloads hosted in Azure.
You have an option to customize the benchmark standards if you have enabled enhanced security features of Microsoft Defender for Cloud. This helps in adhering to organizational specific security compliance requirements. You can also derive the security score for additional industry standard regulations like NIST, ISO 27001, etc. Startups delivering products and services for heavily regulated industries can leverage this feature to meet their regulatory requirements. In addition to Microsoft Azure, you can view the secure score of your Amazon Web Services (AWS)and Google Cloud platform (GCP) deployments from the same interface once you have connected Microsoft Defender for Cloud to these target cloud environments.
Microsoft Defender for Cloud also provides vulnerability assessments of resources like virtual machines, container registries and SQL servers. Some of these scanners use Qualys in the backend, and the integration process is handled transparently by Microsoft Defender for Cloud. The vulnerability assessment service for servers is called Microsoft Defender for Servers which is natively integrated with the industry leading endpoint detection and response (EDR) solution Microsoft Defender for Endpoint. This service uses the built-in Microsoft’s threat and vulnerability management module for real time identification of threats and prioritization of vulnerabilities.
Security hardening of resources
Along with identifying vulnerabilities, security loopholes and misconfigurations Microsoft Defender for Cloud also provides guidance on the action that needs to be taken to remediate the risks and harden the environment. Wherever possible, automated remediation will be available. You can simply click the ‘fix’ button to implement the solution. Where manual intervention is required detailed steps for implementing the solution will be provided so that it will ease the hardening process.
The solution uses the Azure policy controls that can be applied across management groups, Azure subscriptions or tenants. These policies can be tailored to meet organizational specific security requirements. Existing resources or new resources are evaluated against the applied policy. A prioritized list of recommendations is provided that help with hardening of resources to reduce the attack surface and enhance security posture of your cloud environments. The recommendations are based on Azure Security Benchmark, that provides prescriptive guidance for cloud security and compliance.
Defend and protect from threats
The cloud workload protection capabilities of defender for cloud detects threats for your workloads and generates timely alerts to notify the concerned team. This service is powered by the contextual threat intelligence capabilities of Microsoft that is built into Azure along with a range of other products like Office 365 and Windows. The service is capable of providing resource specific threat intelligence, e.g., unauthorized activities in your Azure resources.
Threat detection capabilities of defender for cloud provides cyber kill-chain analysis to correlate generated alerts for your cloud resources and provide visibility into the attack vector including lateral movements and impacted resources. The MITRE ATT&CK matrix version 9 is used as the basis of supported kill chain intents in Microsoft Defender for Cloud. The generated alerts can be streamed to security information and event management (SIEM), security orchestration automation and response (SOAR), and IT service management (ITSM) solutions for further analysis. Microsoft Defender for Cloud also provides advanced threat protection capabilities like just-in-time VM access and adaptive application controls to allow only specific applications to run on your virtual machines.
In addition to Azure resources, Microsoft Defender for Cloud also stands out because of its hybrid and multi-cloud posture management capabilities. It can help secure AWS, GCP and on-prem resources through its CSPM capabilities. The process can either be agent based or agentless. In agent-based protection, a log analytics agent is deployed to collect security information from non-Azure resources. In agentless protection you need to connect AWS or GCP resources to Microsoft Defender for Cloud and benefit from the CSPM capabilities. For example: if you have an AWS environment connected to Microsoft Defender for Cloud, the service can assess the security posture against standards like AWS CIS, AWS PCI DSS and AWS foundational security best practices. You can also view the list of AWS resources in the asset inventory view of Microsoft Defender for Cloud, where unhealthy AWS resources will be flagged for remediation.
Microsoft Defender for Cloud can provide real-time threat protection for the EKS Linux clusters in AWS and generates alerts for suspicious activities. Container protection can be enabled for GKE clusters in Google Cloud by onboarding them to Azure Arc and enabling enhanced security features of Microsoft Defender for cloud. For Windows and Linux machines in AWS and GCP a similar process can be followed to enable threat detection and protection. The service is called Microsoft Defender for Services and provides comprehensive endpoint protection, comprehensive OS level assessment, vulnerability scanning, file integrity monitoring, adaptive application controls, etc.
Get started with Microsoft Defender for Cloud
Microsoft Defender for Cloud has a free plan that is enabled for all Azure resources. It is enabled by default when the page is accessed for the first time from Azure portal. The free plan provides continuous security assessment and recommendations and provides a secure score based on this assessment.
For advanced threat detection and security management, you need to enable the enhanced security features. The enhanced capabilities include resource specific protection for servers, containers, databases, etc. It also provides additional features like regulatory compliance dashboards, threat protection for non-Azure VMs, PaaS services, adaptive application controls, network hardening, just-in-time VM access, etc.
Prerequisites
You should have access to an Azure subscription and have either subscription owner, subscription contributor or security admin status to enable enhanced security features of Microsoft Defender for Cloud.
Enable Defender for Cloud on Azure subscription
From Azure Portal Menu, select “Defender for Cloud” to access the overview:
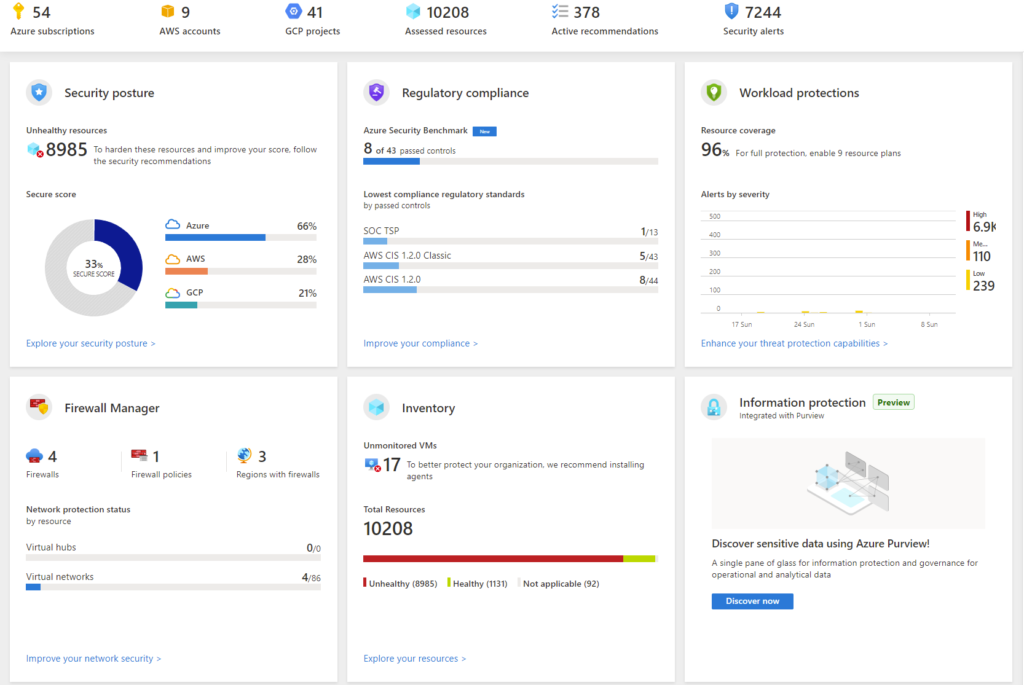
The overview page provides the following information:
- Number of Azure subscriptions, AWS accounts and GCP projects connected to Microsoft Defender. You can select and filter the target cloud environment from here to view details of respective environments.
- Number of connected cloud accounts, security alerts and hardening recommendations are also shown in this page.
There are additional feature tiles in the overview page.
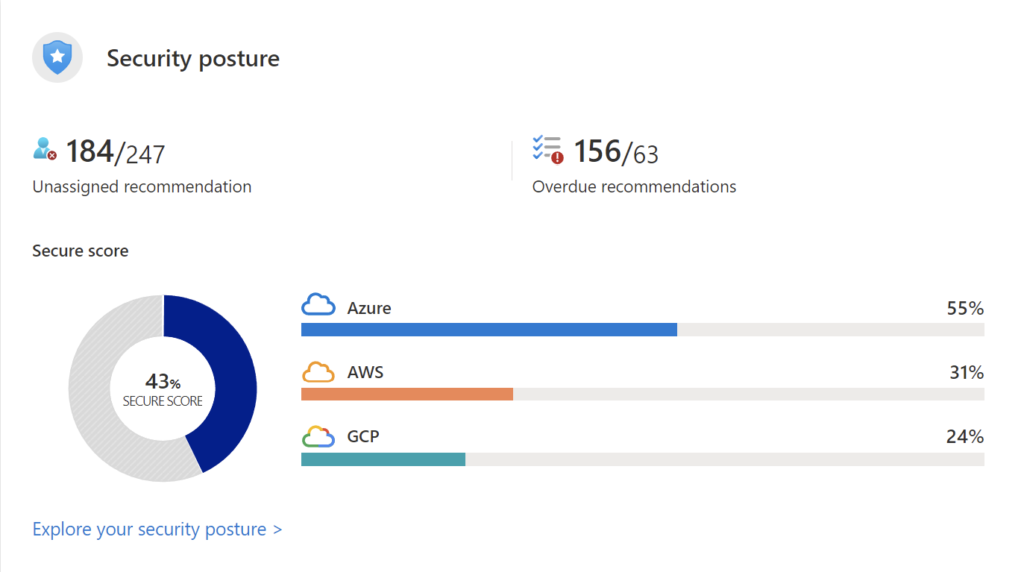
Security posture
The secure score based on continuous assessment of your environment security posture is displayed in this tile. It also provides the count of number of unhealthy resources in your cloud environments.
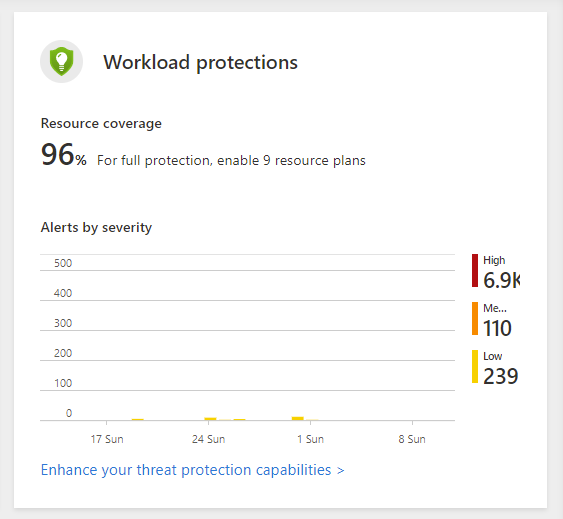
Workload protections
This tile shows the output from CWPP capability of the service, with threat severity segregated as high, medium, and low. The output is based on the respective defender plan tailored for each cloud resource.
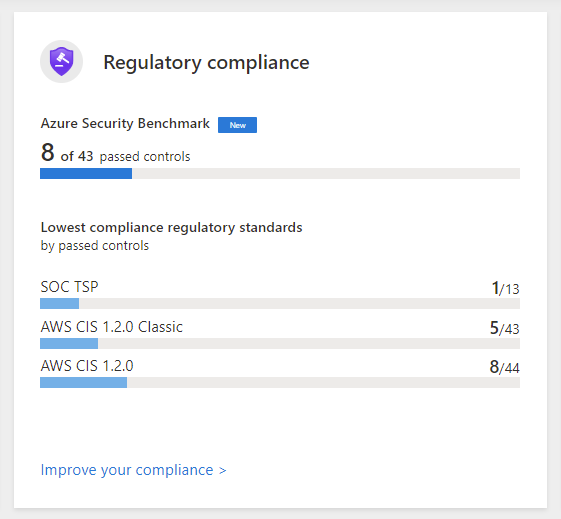
Regulatory compliance
This tile shows the results of compliance assessment against security baselines and regulatory compliance standards. It provides a view based on continuous assessment against compliance standards applicable for your organization, for example: ISO, SOC, PCI, to name a few.
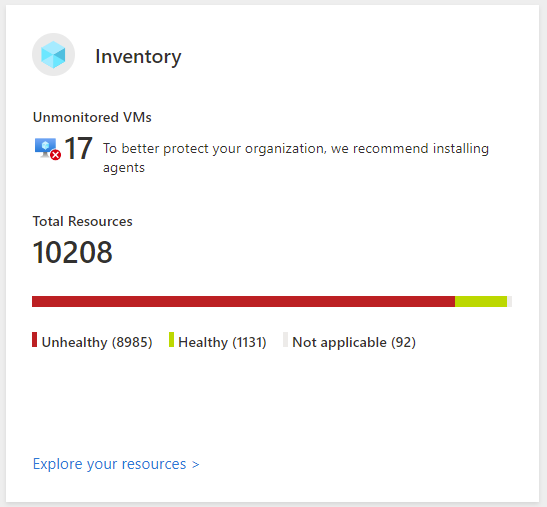
Inventory
This tile provides a consolidated view of security posture of all resources (including Hybrid and multi cloud) connected to Microsoft Defender for cloud. Software inventory collected via Microsoft Defender for server and Microsoft defender for endpoint are also displayed here. It provides a segregated view of healthy and unhealthy resources in your environment.
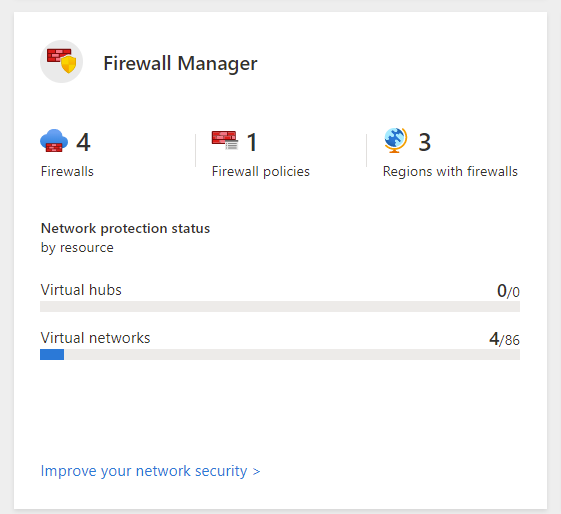
Firewall manager
Azure firewall manager is the centralized security management service for cloud security perimeters that uses either azure virtual WAN Hub or hub virtual network architectures. The firewall manager tile shows the status of security status of these architectures.
Information protection
Microsoft Purview provides data governance and management capabilities for your data estate spread across multi cloud as well as hybrid deployments. If you have enabled Microsoft Purview this tile will show details such an identified sensitive data and associated recommendations and alerts.
Conclusion
As you scale your application landscape in the cloud, security should never be an afterthought. Microsoft Defender for Cloud helps startups reinforce their security posture without huge investments in third party tools, services or teams dedicated to security management. The service aligns with the lean and agile cloud resource management strategy of startups. In the first part of this blog series, we covered an introduction of the capabilities offered by Microsoft defender for cloud for your multi/hybrid cloud workloads. In part II, “How to secure your product infrastructure security” and part III “How to defend your product infrastructure security” we will deep dive into the details of how you can get started with the service and leverage it to ensure comprehensive cloud multi cloud security.
To get started with Microsoft for Startups Founders Hub, sign up today.












